Thundertrike: The First Bootkit For Mac
The out of the 31st Chaos Computer Club conference in Hamburg, Germany last month. Security researcher Trammell Hudson developed the attack and named it Thunderstrike. It exploits a vulnerability deep in the core of the Apple’s OS X operating system. In fact, the vulnerability underlies the operating system altogether.
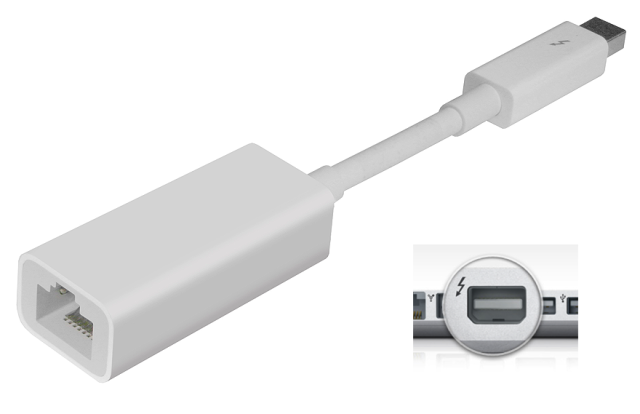
Hudson contacted Apple and they reportedly resolved the issue in all affected devices except the MacBook. There is no room for doubt here: Thunderstrike, is a nasty threat that can wrest control over everything you do on your computer. You can think of it as the Ebola of computer threats: catching the disease carries devastating consequences, but the likelihood of becoming infected is relatively small. Interested in the Apple vulnerability but don't have an hour for the video? — Trammell Hudson™ (@qrs) that live within the boot process beneath your computer’s operating system, commanding complete control over infected machines.
They affect the Master Boot Record and initiate on startup, before the operating system even loads. Even if you delete your operating system, the bootkit remains. Bootkits, therefore, and even difficult to find, though will root them out.
Thunderstrike is a bootkit for OS X devices that can be installed via direct hardware access or through a thunderbolt connection. The first scenario, infection via direct hardware access is unlikely. Either the manufacturer would have to install the bootkit or an attacker would have to take your Macbook apart and physically install it into the hardware him or herself. #Thunderstrike is a #Mac #bootkit that is only transmittable through direct hardware or #Thunderbolt cable access However, the second vector, infection through the Thunderbolt connection, is slightly more viable. In fact, we have a term for this kind of attack: they’re called “evil maid” attacks, or state-sponsored attacks where laptops are confiscated and examined in airports or border crossings.
The same method could be applied any time you are away from your machine. Thus, like Ebola, which is only transmittable through direct contact with bodily fluids, your machine is only susceptible to Thunderstrike if someone takes it apart or sticks a thunderbolt connection into it and installs malicious firmware on your Mac from a peripheral device. It can’t be removed by software since it controls the signing keys and update routines. Reinstallation of OS X won’t remove it. Replacing the SSD won’t remove it since there is nothing stored on the drive. Other pieces of malware are less impactful but have far greater transmission rates. To complete the metaphor, the common cold is airborne, and poses a far greater risk to the general public than Ebola, despite the fact that the common cold is not generally terminal.
Similarly, a piece of malware designed to eat processing power and contribute to a botnet isn’t quite as scary as Thunderstrike, but because it can infect your machine remotely through a web injection, malicious email, drive-by download or a number of other vectors, it’s actually much more of a public nuisance. “Since it is the first OS X firmware bootkit, there is nothing currently scanning for its presence,” Hudson said. “It controls the system from the very first instruction, which allows it to log keystrokes, including disk encryption keys, place backdoors into the OS X kernel and bypass firmware passwords.
It can’t be removed by software since it controls the signing keys and update routines. Reinstallation of OS X won’t remove it. Replacing the SSD won’t remove it since there is nothing stored on the drive.” The best way to protect yourself against Thunderstrike is to make sure that no one can access your Macbook when you aren’t around. In other words, if you are careful about avoiding theft, then you should be good to go. In the meantime, enjoy some AC/DC.
Our innovative products help to give you the Power to Protect what matters most to you. Band-in-a-box 2017 : pro edition for mac. Discover more about our award-winning security.
Our FREE security tools and more can help you check all is as it should be on your PC, Mac or mobile device. Discover more about who we are how we work and why we’re so committed to making the online & mobile world safer for everyone. Try Before You Buy. In just a few clicks, you can get a FREE trial of one of our products – so you can put our technologies through their paces.
. US-based security researcher Trammell Hudson presented an intriguing at the recent Chaos Computer Congress (CCC) in Germany. He called his work, because it makes use of the Mac’s Thunderbolt port to do its dirty work. Hudson decided to see if he could dig a rootkit even more deeply into a Mac than at the kernel or the boot sector level, where it is at least theoretically visible on your hard disk.
He wondered, in fact, if it might be possible to bury a rootkit in the Boot ROM chip on the motherboard. That’s the firmware that runs right at the very start, when the computer is first powered up, and on which depends the correctness and security of everything that follows.
(In modern parlance, the word is usually used to refer to malware that is deliberately designed to stay out of sight, from detection and removal.) The Mac bootstrap Very greatly simplified, the Mac bootup process goes something like this:. Load firmware from the Boot ROM (soldered onto the motherboard). Load firmware Option ROMs from any connected Thunderbolt devices. Load and run the Extensible Firmware Interface (EFI) code. Load and run OS X itself. Generally speaking, any rootkit installed or activated at stage 3 or 4 above can be detected using regular and well-documented programming techniques.
Granted, the rootkit might be very hard to find, and harder yet to remove, but well-informed security researchers will be able to deal with it, even if a special bootup CD or USB image is needed. → That’s the approach taken by (SBAV), which can be used on Windows computers to remove stubborn rootkits. It works by booting up into a special-purpose Linux distribution, without running any executable code from your hard disk at all. This bypasses any and all malicious or damaged components in your Windows installation.
(excellently presented and well-worth reading in full) deals with two aspects of the Mac startup process:. If you open up the Mac’s case and get physical access to the ROM chip, can you rewrite it without triggering an alarm?.

If you can indeed alter the ROM undetected, can you do so without without opening up the Mac’s case? As you can imagine, a rootkit embedded in the Boot ROM itself would be extremely difficult to detect and disinfect. Altering the Boot ROM Hudson started by opening up his Mac’s case and altering the contents of the Boot ROM directly. (The ROM chip is actually an Electrically Erasable Programmable ROM, or EEPROM.) He did this by wiring an EEPROM reprogrammer of his own devising directly to the contacts of the chip. He performed the following simple but telling experiments:.
Make an otherwise harmless one-byte change in the ROM. The Mac booted from the ROM; the cooling fans started for a moment, but then stopped when the computer shut itself down. Change the very first code instruction in the ROM into an infinite loop. The Mac booted; the cooling fans started, and kept on running. Conclusion: there is some sort of Boot ROM checksum test that can shut down your Mac. But the shutdown is performed by code inside the ROM itself; therefore it can be bypassed or removed. Altering the ROM without opening the case So, serious adversaries who are determined to target your Mac with a ROM-based surveillance rootkit can, in theory, do so.
They’ll need to separate you from your computer for long enough to open it up, disconnect the battery, attach wires to the Boot ROM, reflash it, and close everything up again so that you don’t notice. But what about an attacker with less time – for example, a so-called “evil maid”? That’s jargon for a hypothetically crooked hotel cleaner who is familiar with computers, and has a legitimate purpose for going in and out of your room when you aren’t there.
(For reasons presumably rooted in the male dominance of the IT industry, crooked cleaners are assumed to be female.) You can easily boot a Mac off USB, of course, but by that time in the bootstrap process, the Boot ROM chip is already locked down into read-only mode. And you can plug in a Thunderbolt device, such as an Ethernet (LAN) adapter, which contains a special sort of subsidiary boot ROM called an Option ROM, which gives you earlier “evil maid” access than a USB-based boot.
But Option ROMs also run after the Boot ROM has switched itself into read-only mode. Subverting the Option ROM process Hudson’s research revealed a loophole in the bootstrap process. So that Apple can ship Boot ROM firmware updates, it is possible to reboot a Mac while leaving the Boot ROM in read-write mode. But this sort of bootstrap is a special one during which all you are supposed to be able to do is write a new firmware image into the ROM and reboot. The current ROM includes a public key to check the digital signature of the new ROM image first; so, in theory, an Apple ROM can rewrite itself with a digitally-signed Apple ROM, and that’s that. But, as Hudson discovered, Thunderbolt Option ROMs run even in “Boot ROM firmware update” mode, despite the fact that they are totally unnecessary under those circumstances.
Worse still, the code in an Option ROM can modify the contents of the firmware update after its digital signature has been verified, but before it gets written to the Boot ROM. Abusing a LAN adaptor Interestingly, Apple’s readily-available Thunderbolt Ethernet dongle has a user-rewritable Option ROM, but it doesn’t have enough storage space to hold a complete replacement Boot ROM image. Hudson found a rather diabolical way around this problem: rewrite only a tiny part of the existing Boot ROM, namely the public key used by the ROM itself to validate its updates. By doing this, not only does he open up the Boot ROM to be reflashed a second time with a firmware image signed by his own private key, but he’s now the only guy who can unflash the rootkit later on.
Even if you suspect (or detect) his shenanigans, you can’t easily flash your Mac back to “Apple Normal Form,” because Apple’s legitimate firmware ROMs are signed with Apple’s private key, not Tramell Hudson’s! Sadly, there’s no easy way to prevent your Mac from being at the moment. Fortunately, Hudson reports that Apple is working on an official change that will prevent Option ROMs from running during a firmware update.
That will prevent his trick of abusing an Option ROM to subvert the Boot ROM update process. In the meantime, we recommend that you don’t leave your Mac – or, indeed, any computer you own – unattended when you travel, if you can possibly help it. In fact, even after Apple ships this fix, we think you should carry your computer equipment with you whenever you can. Especially when the only place to leave it is somewhere that you know will be visited by other people (e.g. Unsupervised hotel cleaners) when you are not there. By the way, if you are worried about your computer being opened up without you realising, try an anti-rootkit trick presented at the 2013 Chaos Computer Congress.
Paint over the case screws and take close-up photos. Sounds bizarre, but, in theory, the glitter sets into a hardware-random pattern that cannot reliably be reproduced after the screws have been opened and the nail polish chipped. An attacker can repaint the screws to look very similar to how they were before, but not identical. The things you can learn from the CCC! Image of courtesy of. Image of courtesy of. Follow for the latest computer security news.
Thunderstrike The First Rootkit For Mac
Follow for exclusive pics, gifs, vids and LOLs!