Synful Packet: Firefox And Java For Mac
Intro For several months, Talos has been working with public- and private-sector threat intelligence partners and law enforcement in researching an advanced, likely state-sponsored or state-affiliated actor's widespread use of a sophisticated modular malware system we call 'VPNFilter.' We have not completed our research, but recent events have convinced us that the correct way forward is to now share our findings so that affected parties can take the appropriate action to defend themselves. In particular, the code of this malware overlaps with versions of the BlackEnergy malware — which was responsible for multiple large-scale attacks that targeted devices in Ukraine. While this isn't definitive by any means, we have also observed VPNFilter, a potentially destructive malware, actively infecting Ukrainian hosts at an alarming rate, utilizing a command and control (C2) infrastructure dedicated to that country. Weighing these factors together, we felt it was best to publish our findings so far prior to completing our research. Publishing early means that we don't yet have all the answers — we may not even have all the questions — so this blog represents our findings as of today, and we will update our findings as we continue our investigation.
Both the scale and the capability of this operation are concerning. Working with our partners, we estimate the number of infected devices to be at least 500,000 in at least 54 countries. The known devices affected by VPNFilter are Linksys, MikroTik, NETGEAR and TP-Link networking equipment in the small and home office (SOHO) space, as well at QNAP network-attached storage (NAS) devices.
No other vendors, including Cisco, have been observed as infected by VPNFilter, but our research continues. The behavior of this malware on networking equipment is particularly concerning, as components of the VPNFilter malware allows for theft of website credentials and monitoring of Modbus SCADA protocols. Lastly, the malware has a destructive capability that can render an infected device unusable, which can be triggered on individual victim machines or en masse, and has the potential of cutting off internet access for hundreds of thousands of victims worldwide. The type of devices targeted by this actor are difficult to defend. They are frequently on the perimeter of the network, with no intrusion protection system (IPS) in place, and typically do not have an available host-based protection system such as an anti-virus (AV) package. We are unsure of the particular exploit used in any given case, but most devices targeted, particularly in older versions, have known public exploits or default credentials that make compromise relatively straightforward.
All of this has contributed to the quiet growth of this threat since at least 2016. This post provides the technical findings you would normally see in a Talos blog. In addition, we will detail some thoughts on the tradecraft behind this threat, using our findings and the background of our analysts, to discuss the possible thought process and decisions made by the actor. We will also discuss how to defend against this threat and how to handle a device that may be infected. Finally, we will share the IOCs that we have observed to this point, although we are confident there are more that we have not seen. Brief technical breakdown The VPNFilter malware is a multi-stage, modular platform with versatile capabilities to support both intelligence-collection and destructive cyber attack operations. The stage 1 malware persists through a reboot, which sets it apart from most other malware that targets internet-of-things devices because malware normally does not survive a reboot of the device.
The main purpose of stage 1 is to gain a persistent foothold and enable the deployment of the stage 2 malware. Stage 1 utilizes multiple redundant command and control (C2) mechanisms to discover the IP address of the current stage 2 deployment server, making this malware extremely robust and capable of dealing with unpredictable C2 infrastructure changes. The stage 2 malware, which does not persist through a reboot, possesses capabilities that we have come to expect in a workhorse intelligence-collection platform, such as file collection, command execution, data exfiltration and device management. However, some versions of stage 2 also possess a self-destruct capability that overwrites a critical portion of the device's firmware and reboots the device, rendering it unusable. Based on the actor's demonstrated knowledge of these devices, and the existing capability in some stage 2 versions, we assess with high confidence that the actor could deploy this self-destruct command to most devices that it controls, regardless of whether the command is built into the stage 2 malware. In addition, there are multiple stage 3 modules that serve as plugins for the stage 2 malware.
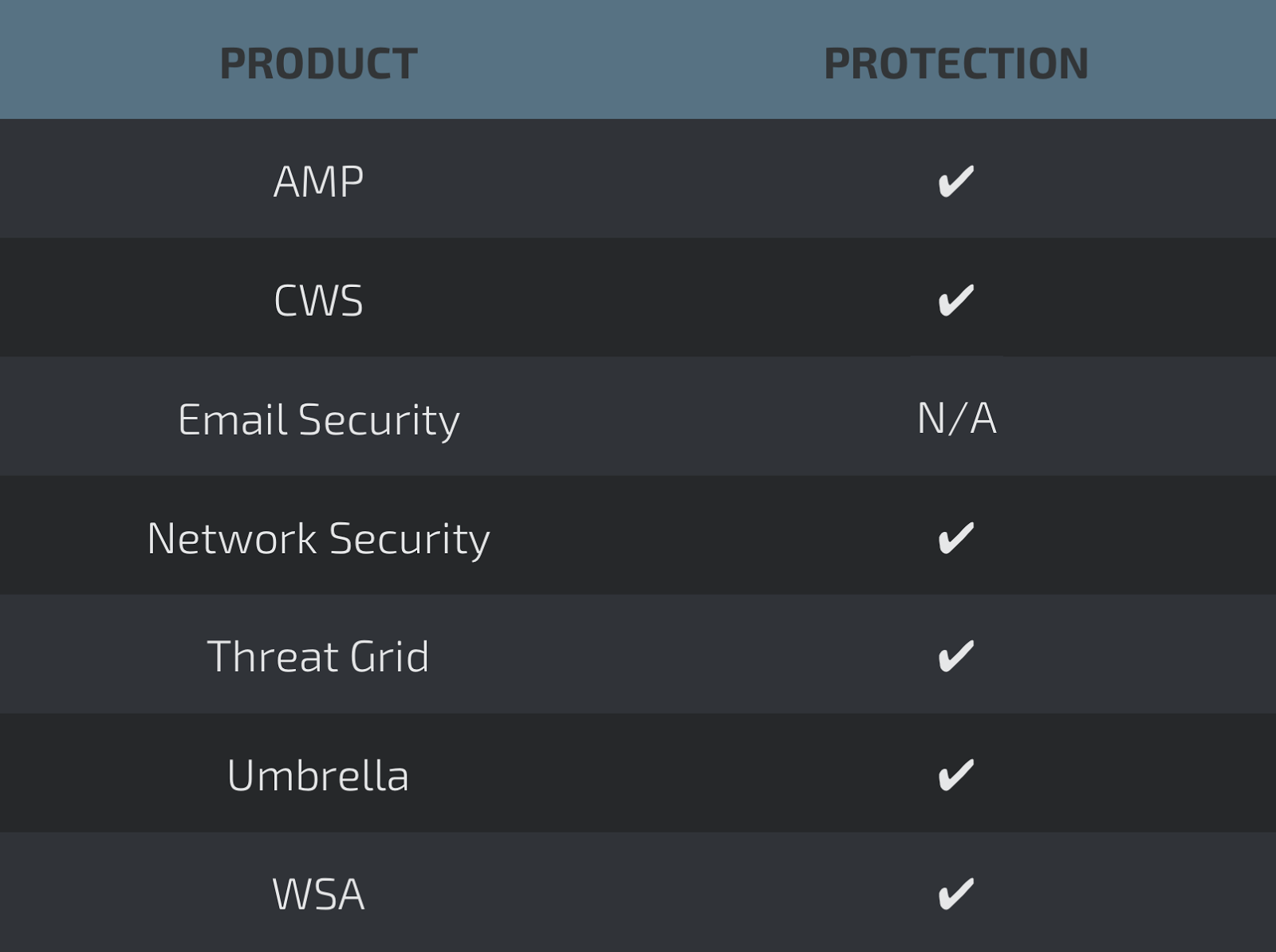
These plugins provide stage 2 with additional functionality. As of this writing, we are aware of two plugin modules: a packet sniffer for collecting traffic that passes through the device, including theft of website credentials and monitoring of Modbus SCADA protocols, and a communications module that allows stage 2 to communicate over Tor. We assess with high confidence that several other plugin modules exist, but we have yet to discover them. Tradecraft discussion We assess with high confidence that this malware is used to create an expansive, hard-to-attribute infrastructure that can be used to serve multiple operational needs of the threat actor. Since the affected devices are legitimately owned by businesses or individuals, malicious activity conducted from infected devices could be mistakenly attributed to those who were actually victims of the actor. The capabilities built into the various stages and plugins of the malware are extremely versatile and would enable the actor to take advantage of devices in multiple ways.

Advanced threat actors, including nation-states, will try to make attribution of their cyber activities extremely difficult, unless it is in their interest for it to be openly known that they conducted a specific act. To this end, advanced threat actors use multiple techniques, including co-opting infrastructure owned by someone else to conduct their operations. The actor could easily use devices infected with this malware as hop points before connecting to their final victim in order to obfuscate their true point of origin. The malware can also be leveraged to collect data that flows through the device. This could be for straightforward data-collection purposes, or to assess the potential value of the network that the device serves. If the network was deemed as having information of potential interest to the threat actor, they may choose to continue collecting content that passes through the device or to propagate into the connected network for data collection. At the time of this posting, we have not been able to acquire a third-stage plugin that would enable further exploitation of the network served by the device.
However, we have seen indications that it does exist, and we assess that it is highly likely that such an advanced actor would naturally include that capability in malware that is this modular. Finally, this malware could be used to conduct a large-scale destructive attack by using the 'kill' command, which would render some or all of the physical devices unusable. This command is present in many of the stage 2 samples we've observed, but could also be triggered by utilizing the 'exec' command available in all stage 2 samples. In most cases, this action is unrecoverable by most victims, requiring technical capabilities, know-how, or tools that no consumer should be expected to have. We are deeply concerned about this capability, and it is one of the driving reasons we have been quietly researching this threat over the past few months. Observed activities of concern As we have researched this threat, we have put into place monitoring and scanning to gain an understanding of the scope of this threat and the behaviors of infected devices. Our analysis has shown that this is a global, broadly deployed threat that is actively seeking to increase its footprint.
While our research continues, we have also observed activity potentially associated with this actor that indicates possible data exfiltration activity. In early May, we observed infected devices conducting TCP scans on ports 23, 80, 2000 and 8080. These ports are indicative of scanning for additional Mikrotik and QNAP NAS devices, which can be found using these ports. These scans targeted devices in more than 100 countries. We also used our telemetry to discover potentially infected devices globally. We evaluated their collective behavior to try and identify additional features of the C2 infrastructure. Many of these victim IPs appeared to demonstrate behavior that strongly indicated data exfiltration.
Finally, on May 8, we observed a sharp spike in VPNFilter infection activity. Almost all of the newly acquired victims were located in Ukraine. Also of note, a majority of Ukrainian infections shared a separate stage 2 C2 infrastructure from the rest of the world, on IP 46.151.209.33. By this point, we were aware of the code overlap between BlackEnergy and VPNFilter and that the timing of previous attacks in Ukraine suggested that an attack could be imminent. Given each of these factors, and in consultation with our partners, we immediately began the process to go public before completing our research. As we continued to move forward with the public disclosure, we observed another substantial increase in newly acquired VPNFilter victims focused in Ukraine on May 17.
Synful Packet Firefox And Java For Mac
This continued to drive our decision to publish our research as soon as possible. New observed VPNFilter infections over time Defending against this threat Defending against this threat is extremely difficult due to the nature of the affected devices. The majority of them are connected directly to the internet, with no security devices or services between them and the potential attackers. This challenge is augmented by the fact that most of the affected devices have publicly known vulnerabilities which are not convenient for the average user to patch. Additionally, most have no built-in anti-malware capabilities. These three facts together make this threat extremely hard to counter, resulting in extremely limited opportunities to interdict malware, remove vulnerabilities, or block threats.
Despite these challenges, Talos has released protections for this threat from multiple angles, to try to take advantage of the limited options that exist. We developed and deployed more than 100 Snort signatures for the publicly known vulnerabilities for the devices that are associated with this threat. These rules have been deployed in the public Snort set, and can be used by anyone to help defend their devices.
In addition, we have done the usual blacklisting of domains/IPs as appropriate and convicting of the hashes associated with this threat to cover those who are protected by the Cisco Security ecosystem. We have reached out to Linksys, Mikrotik, Netgear, TP-Link and QNAP regarding this issue.
(Note: QNAP has been aware of certain aspects of VPNFilter and previously done work to counter the threat.) Finally, we have also shared these indicators and our research with international law enforcement and our fellow members of the in advance of this publication so they could move quickly to help counter this threat more broadly. Recommendations We recommend that:. Users of SOHO routers and/or NAS devices reset them to factory defaults and reboot them in order to remove the potentially destructive, non-persistent stage 2 and stage 3 malware. Internet service providers that provide SOHO routers to their users reboot the routers on their customers' behalf. If you have any of the devices known or suspected to be affected by this threat, it is extremely important that you work with the manufacturer to ensure that your device is up to date with the latest patch versions. If not, you should apply the updated patches immediately. ISPs work aggressively with their customers to ensure their devices are patched to the most recent firmware/software versions.
Due to the potential for destructive action by the threat actor, we recommend out of an abundance of caution that these actions be taken for all SOHO or NAS devices, whether or not they are known to be affected by this threat. Multi-Stage Technical Details Exploitation At the time of this publication, we do not have definitive proof on how the threat actor is exploiting the affected devices. However, all of the affected makes/models that we have uncovered had well-known, public vulnerabilities. Since advanced threat actors tend to only use the minimum resources necessary to accomplish their goals, we assess with high confidence that VPNFilter required no zero-day exploitation techniques.
Stage 1 (persistent loader) VPNFilter's stage 1 malware infects devices running firmware based on Busybox and Linux, and is compiled for several CPU architectures. The main purpose of these first-stage binaries is to locate a server providing a more fully featured second stage, and to download and maintain persistence for this next stage on infected devices.
It is capable of modifying non-volatile configuration memory (NVRAM) values and adds itself to crontab, the Linux job scheduler, to achieve persistence. This is a departure from previous IoT malware, like Mirai, which is ephemeral and disappears with a simple device reboot. Talos analyzed samples for MIPS and x86 processors.
Synful Packet: Firefox And Java For Mac Free
The C2 communication and additional malware downloads occur over Tor or SSL-encrypted connections. While the binaries themselves are not obfuscated beyond being stripped, some strings are stored in an encrypted form, and are only decrypted at runtime. The decryption routine looked suspiciously similar to RC4 in the static analysis, but it looks like the malware authors got the initialization of the S-boxes wrong.
During the permutation step, values are XOR’d, but not swapped. Analysis of this RC4 implementation shows that it is identical to the implementation used in BlackEnergy, which is. VPNFilter specific Snort detection: 4 3 Snort rules that protect against known vulnerabilities in affected devices: 6 8 0 3 1 3 5 7 2 4 1 8 0 5 7 9 5 0 2 7 5 3 0 4 6 8 0 9 1 8 9 2 4 8 3 7 45157 ClamAV Signatures: Unix.Trojan.Vpnfilter-6425811-0 Unix.Trojan.Vpnfilter-6425812-0 Unix.Trojan.Vpnfilter-6550590-0 Unix.Trojan.Vpnfilter-6550591-0 Unix.Trojan.Vpnfilter-6550592-0.
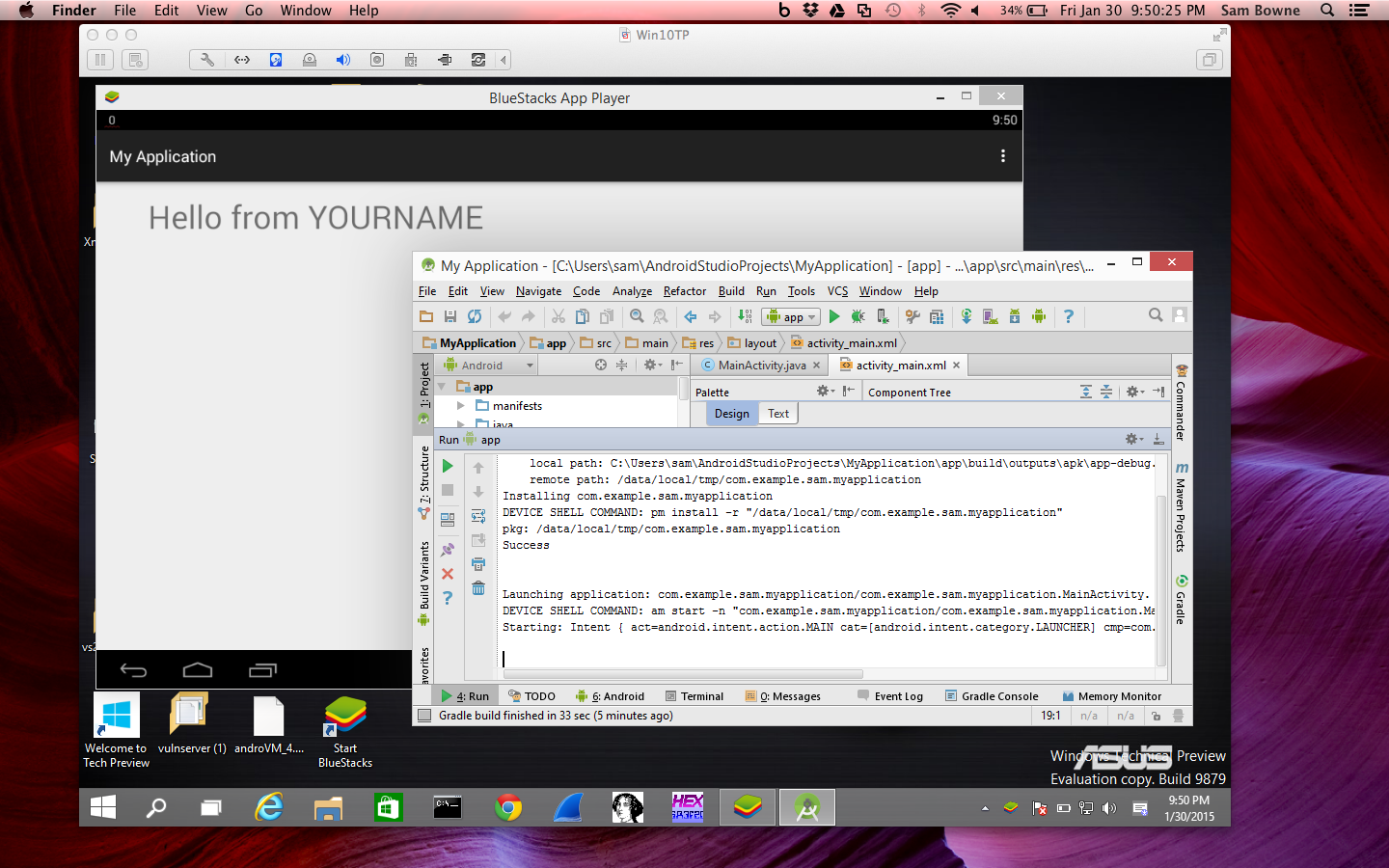
Up until yesterday I've been using Firefox ESR 52.1.0 (64-bit) in order to access a VPN I need for work, which requires a Java plugin. I'm also running Firefox Developer Edition 54.0a2 (2017-04-20) (64-bit).
Yesterday I updated Java to 'Version 8 Update 131 (build 1.8.0131-b11)', and I can longer use Java plugins on any version of Firefox, which means I can no longer access the VPN. It was my understanding that The ESR versions of Firefox would continue to support Java through into 2018, but this has not been my experience. Are there any specific issues with these versions of Firefox that prevent Java Plugins from working, or is this an issue with that version of Java itself? Up until yesterday I've been using Firefox ESR 52.1.0 (64-bit) in order to access a VPN I need for work, which requires a Java plugin. I'm also running Firefox Developer Edition 54.0a2 (2017-04-20) (64-bit). Yesterday I updated Java to 'Version 8 Update 131 (build 1.8.0131-b11)', and I can longer use Java plugins on any version of Firefox, which means I can no longer access the VPN. It was my understanding that The ESR versions of Firefox would continue to support Java through into 2018, but this has not been my experience.
Are there any specific issues with these versions of Firefox that prevent Java Plugins from working, or is this an issue with that version of Java itself? After almost a day of messing around with various configuration options for Java, Firefox and a few other browsers trying to get this thing to work again, rolling back to Java V8 121, whilst not an ideal solution, seems to have done the trick. For anyone else using a Checkpoint SSL Network Extender on a Mac, I suggest not updating Java until they start supporting browsers other than IE again.
Synful Packet: Firefox And Java For Mac Windows 10
Note that the Firefox 54.0 DE version has been discontinued and users will be moved over to the beta version.The current Firefox 52.1.1 esr version should still support the Java plugin AFAIK. Make sure that you have the Java plugin present in the correct location in case the Java updater didn't do this properly. /Library/Internet Plug-Ins. /Library/Internet Plug-Ins In Mac OS X v10.7 and later, the /Library folder is a hidden folder. Websites will have to use Java Web Start to launch a Java application in an external standalone window instead of using an applet to open this embedded in a web page. A Java Web Start JNLP file is basically a XML file that the server sends as application/x-java-jnlp-file and that is opened by the default application for this MIME type (Java Web Start). Java then handles everything on its own, but there is no longer embedding possible like a plugin offers.
Java registers this MIME type when you install the Java program. Websites will have to use Java Web Start to launch a Java application in an external standalone window instead of using an applet to open this embedded in a web page. A Java Web Start JNLP file is basically a XML file that the server sends as application/x-java-jnlp-file and that is opened by the default application for this MIME type (Java Web Start). Java then handles everything on its own, but there is no longer embedding possible like a plugin offers. Java registers this MIME type when you install the Java program.